Attacks on PDF Certification (May 2021)
The PDF specification defines two types of digital signatures:
Approval signatures testify a specific document state. The specification allows the usage of multiple signatures on the same document. Any other change on a signed document leads to an invalidation of the approval signature or warnings in most PDF viewers. Hereafter, we use the terms signature and signed document for approval signatures.
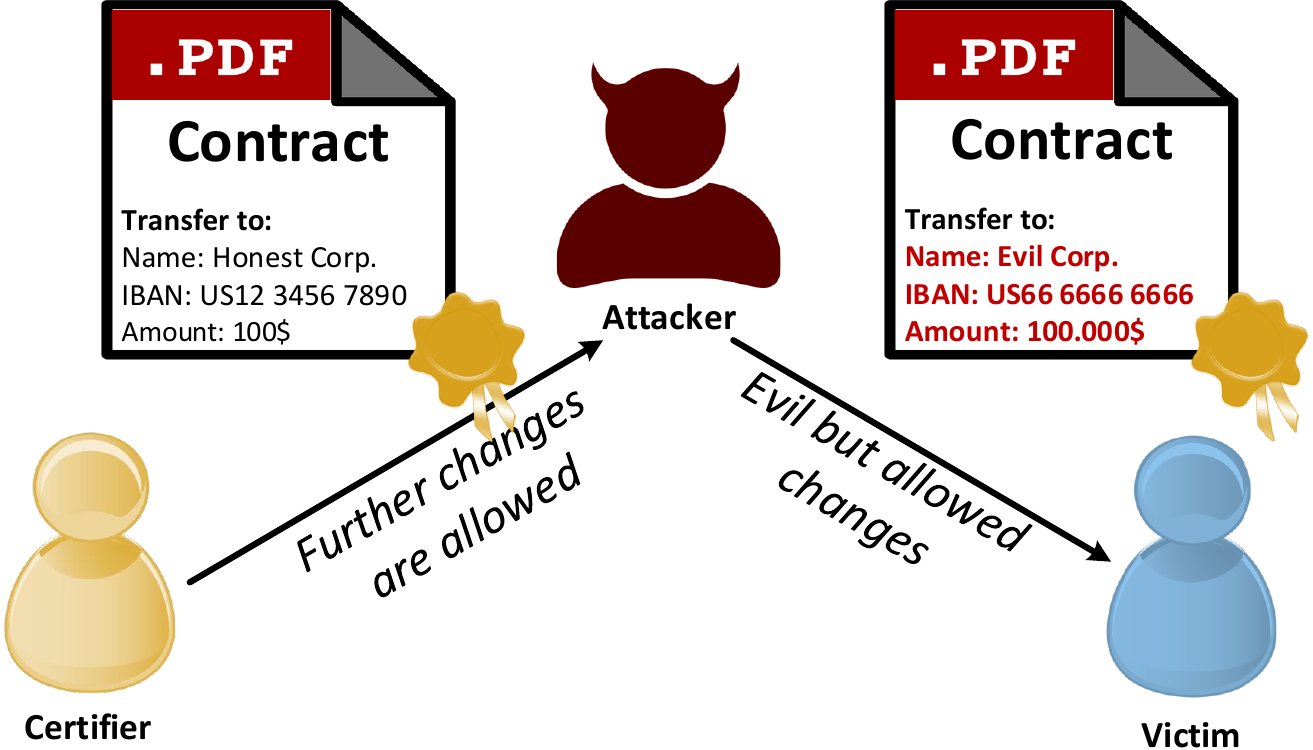
Certification signatures provide a more powerful and flexible mechanism to handle digitally signed documents. During the document’s certification, the owner defines a list of allowed modifications that do not invalidate the document’s certification signature. These allowed modifications can be a subset of the following actions: writing text to specific form fields (even without signing the document), providing annotations to the document, or adding approval signatures. Since a certification signature sets permissions on the entire document, only one certification signature is allowed within a PDF document. This certification signature must also be the first signature in the PDF. Hereafter, we use the terms certification and certified document for certification signatures.
So what is the problem?
We investigate the following question: How dangerous are permitted changes in certified documents?. To answer this question we systematically analyze the allowed modifications in certified documents and reveal two new vulnerabilities abusing flaws in the PDF specification: Evil Annotation Attack (EAA) and Sneaky Signature Attack (SSA). These vulnerabilities allow an attacker to change the visible content of a PDF document by displaying malicious content over the certified content. Nevertheless, the certification remains valid and the application shows no warnings.
How bad is it?
We evaluated 26 PDF applications and were able to break the security of certified documents in 24 of them. Additionally, we analyzed 26 applications to determine whether the permissions for adding annotations and signatures, as defined in the PDF specification, were implemented correctly. We show that for 11 of 26 applications, a permission mismatch exists.
The detailed results of our study can be found in the Evaluation and in our Paper (S&P'21).
Code Injection Attack on Adobe: Only certified documents may execute high privileged JavaScript code in Adobe products. For example, a high-level JavaScript can call an arbitrary URL without user confirmation to deanonymize a user. Our research reveals that such code is also executed if it is added as an allowed incremental update. We are the first to reveal that this behavior allows attackers to directly embed malicious code into a certified document.
My PDF Reader is not listed
If you use another Reader, you should contact the support team for your application. Alternatively, you can use the provided Exploits to test your application.
Technical Details
Insecure Features in PDFs (January 2021)
It is common to open PDF files from potentially untrusted sources such as email attachments or downloaded from the Internet. This time, we perform an in-depth analysis of the capabilities of malicious PDF documents. Instead of focusing on implementation bugs, we abuse legitimate features of the PDF standard itself by systematically identifying dangerous paths in the PDF file structure.
These dangerous paths lead to attacks that we categorize into four generic classes: (1) Denial-of-Service attacks affecting the host that processes the document. (2) Information disclosure attacks leaking personal data out of the victim’s computer. (3) Data manipulation on the victim’s system. (4) Code execution on the victim’s machine.
So what is the problem?
The PDF standard supports numerous advanced features, ranging from cryptography to calculation logic, 3D animations, JavaScript, up to form fields. A PDF document can be updated or annotated without losing previous revisions and defines specific actions, for example, to display a specific page once the viewer opens the document. On top of this, PDF is enriched with different data formats which can be embedded into documents, such as XML, or Flash. Each of the formats has its strengths, but allowing their inclusion also enables their weaknesses and concerns.
How bad is it?
An evaluation of 28 popular PDF processing applications shows that 26 of them are vulnerable at least one attack. The detailed results of our study can be found in the Evaluation and in our Paper.
We reported our attacks and findings to the affected vendors and proposed appropriate countermeasures, resulting in CVE-2020-28352, CVE-2020-28353, CVE-2020-28354, CVE-2020-28355, CVE-2020-28356, CVE-2020-28357, CVE-2020-28358, CVE-2020-28359, CVE-2020-28410, CVE-2020-28411, and CVE-2020-28412.
My PDF Reader is not listed
If you use another Reader, you should contact the support team for your application. Alternatively, you can use the provided Exploits to test your application.
Technical Details
Shadow Attacks (July 2020)
In the analog world, handwritten signatures are typically added at the end of the document. This has one major downside: it is possible to exchange all pages before the signed page with arbitrary content. This exchange is impossible when using digital signatures because digital signatures protect the entire content of a document. So it is assumed that such an attack from the analog world cannot be transferred to digital signatures.
What is a Shadow Attack?
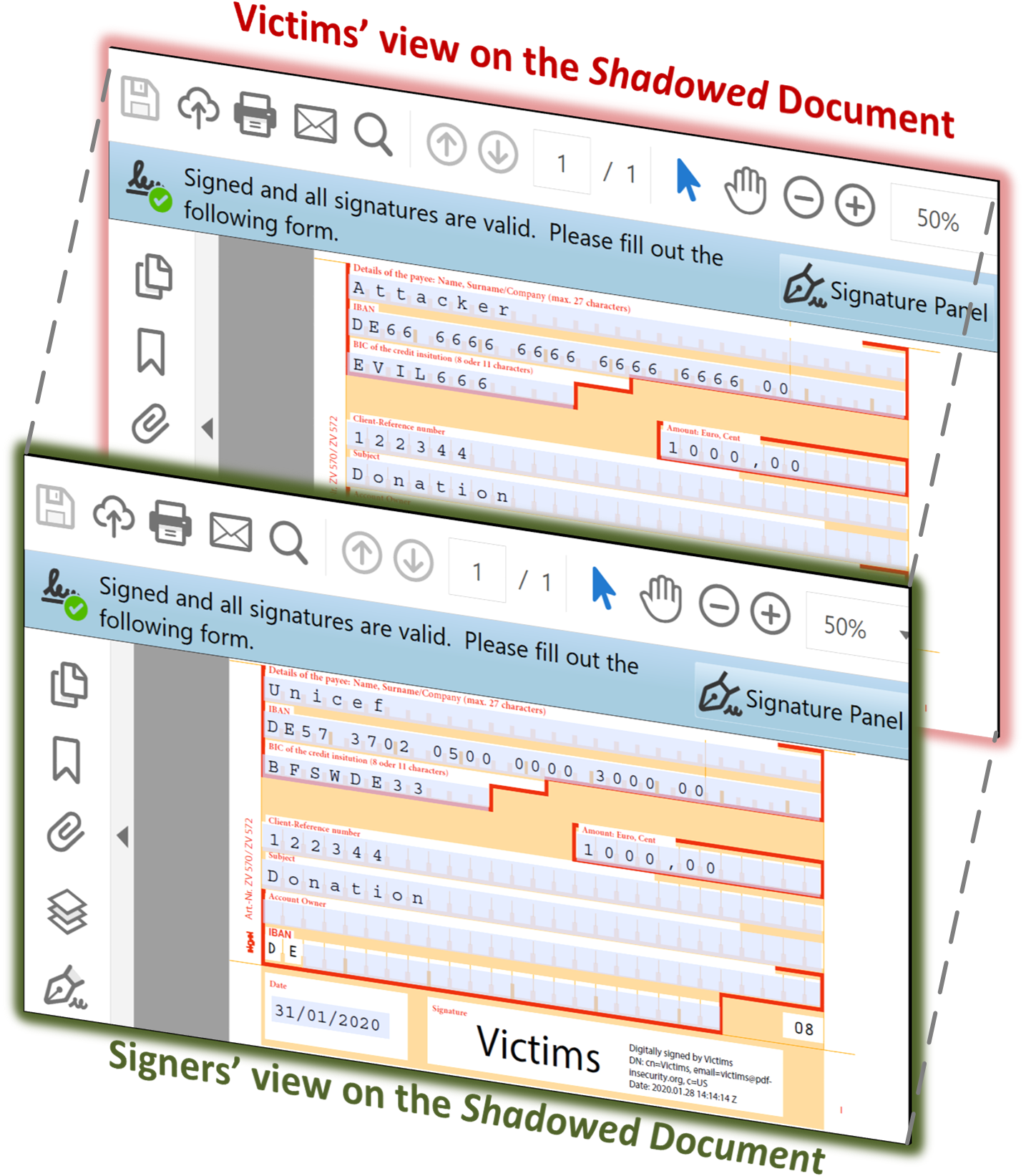 We show that this assumption is incorrect by introducing a new attack class: *Shadow Attacks*.
The idea of Shadow Attacks is that the attackers create a PDF document with two different contents:
We show that this assumption is incorrect by introducing a new attack class: *Shadow Attacks*.
The idea of Shadow Attacks is that the attackers create a PDF document with two different contents:
- content expected by the authority reviewing and signing the PDF and
- hidden content that will be displayed after the PDF is signed.
The Signers of the PDF receive the document, review it, and sign it. The attackers use the signed document, modify it slightly, and send it to the victims. After opening the signed PDF, the victims check whether the digital signature was successfully verified. However, the victims see different content than the Signers.
We introduce three different variants of the Shadow Attacks, allowing attackers to Hide, Replace, and Hide-and-Replace content in digitally signed PDFs.
So what is the problem?
Based on the ISA attacks that we discovered in Feb 2019, the PDF applications analyze the changes made after signing and try to estimate if these changes are legitimate. For instance, overwriting content on a page of the document is not allowed and thus leads to invalid signature verification. Nevertheless, some changes are considered harmless by the PDF applications and do not throw any warnings. We analyzed these legitimate changes and abused these to exchange the entire content within a PDF document.
How bad is it?
During our research, we identified 15 out of 28 desktop viewer applications vulnerable to at least one of our attacks. You can find the detailed results of our evaluation on the following web page: Desktop Viewer Applications
We started a responsible disclosure procedure on 2nd of March 2020. In cooperation with the CERT-Bund, we contacted all vendors, provided proof-of-concept exploits, and helped them to fix the issues. The attacks are documented in CVE-2020-9592 and CVE-2020-9596.
You can find the report and all exploits on the following web page: Report and Exploits to test your application.
My PDF Reader is not listed
If you use another Reader, you should contact the support team for your application. Alternatively, you can use the provided Exploits to test your application.
Technical Details
How to break PDF Encryption (November 2019)
To guarantee confidentiality, PDF files can be encrypted. This enables the secure transfer and storing of sensitive documents without any further protection mechanisms.
The key management between the sender and recipient may be password based (the recipient must know the password used by the sender, or it must be transferred to them through a secure channel) or public key based (i.e., the sender knows the X.509 certificate of the recipient).
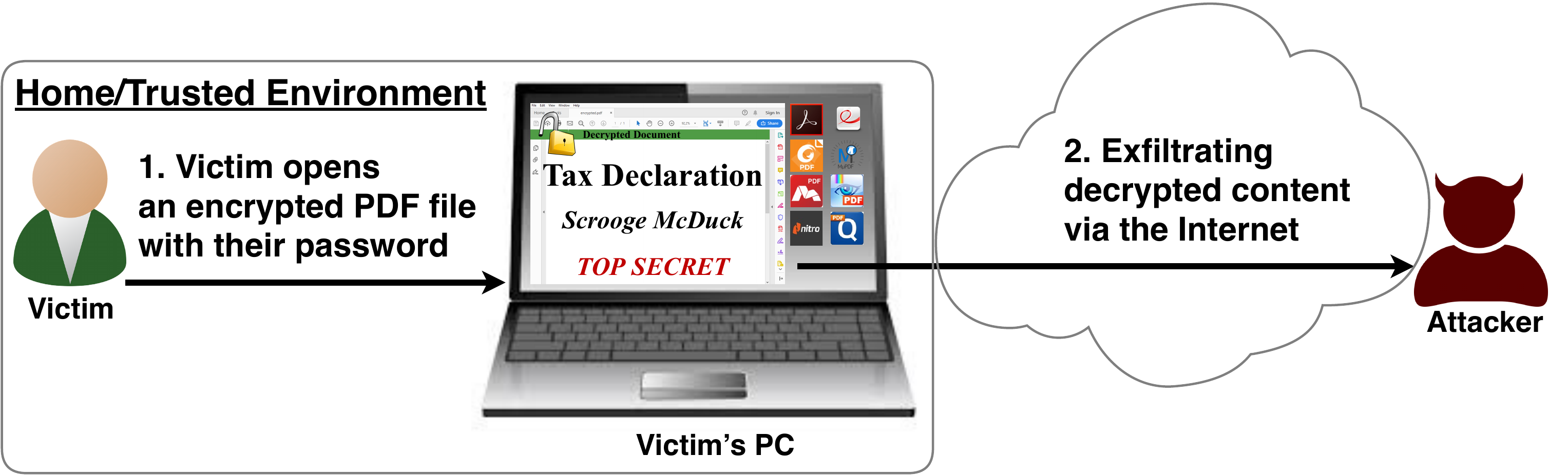
In this research, we analyze the security of encrypted PDF files and show how an attacker can exfiltrate the content without having the corresponding keys.
So what is the problem?
The security problems known as PDFex discovered by our research can be summarized as follows:
Even without knowing the corresponding password, the attacker possessing an encrypted PDF file can manipulate parts of it.
More precisely, the PDF specification allows the mixing of ciphertexts with plaintexts. In combination with further PDF features which allow the loading of external resources via HTTP, the attacker can run direct exfiltration attacks once a victim opens the file.
PDF encryption uses the Cipher Block Chaining (CBC) encryption mode with no integrity checks, which implies ciphertext malleability.
This allows us to create self-exfiltrating ciphertext parts using CBC malleability gadgets. We use this technique not only to modify existing plaintext but to construct entirely new encrypted objects.
You can use the following logo for referencing the PDFex attacks (Creative Commons Licence).

Who uses PDF Encryption?
PDF encryption is widely used. Prominent companies like Canon and Samsung apply PDF encryption in document scanners to protect sensitive information.
Further providers like IBM offer PDF encryption services for PDF documents and other data (e.g., confidential images) by wrapping them into PDF. PDF encryption is also supported in different medical products to transfer health records, for example Innoport, Ricoh, Rimage.
Due to the shortcomings regarding the deployment and usability of S/MIME and OpenPGP email encryption, some organizations use special gateways to automatically encrypt email messages as encrypted PDF attachments, for example CipherMail, Encryptomatic, NoSpamProxy. The password to decrypt these PDFs can be transmitted over a second channel, such as a text message (i.e., SMS).
How bad is it?
In order to measure the impact of the vulnerabilities in the PDF specification, we analyzed 27 widely used PDF viewers. We found 23 of them (85%) to be vulnerable to direct exfiltration attacks and all of them to be vulnerable to CBC gadgets.
You can find the detailed results of our evaluation here.
How can I protect myself?
We strictly followed the responsible disclosure procedure by reporting the results on 17th of May 2019. In cooperation with the CERT-Bund, we contacted all affected vendors, provided proof-of-concept exploits, and helped them to mitigate the issues.
You can take a look at which PDF Reader you are using and compare the versions, see Evaluation.
My PDF Reader is not listed
If you use another Reader, you should contact the support team for your application.
Technical Details
How to break PDF Signatures (November 2019)
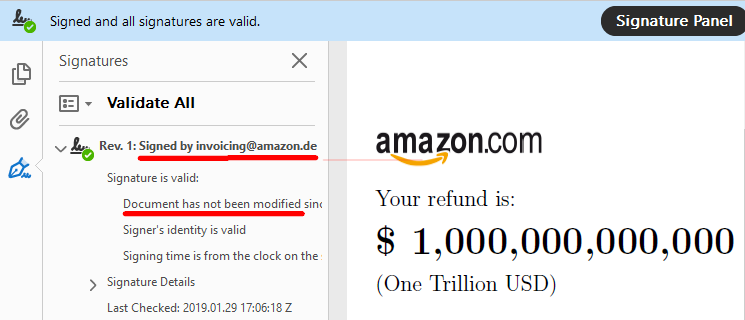
If you open a PDF document and your viewer displays a panel (like you see below) indicating that
- the document is signed by invoicing@amazon.de and
- the document has not been modified since the signature was applied You assume that the displayed content is precisely what invoicing@amazon.de has created.
During recent research, we found out that this is not the case for almost all PDF Desktop Viewers and most Online Validation Services.
So what is the problem?
With our attacks, we can use an existing signed document (e.g., amazon.de invoice) and change the content of the document arbitrarily without invalidating the signatures. Thus, we can forge a document signed by invoicing@amazon.de to refund us one trillion dollars.
To detect the attack, you would need to be able to read and understand the PDF format in depth. Most people are probably not capable of such thing (PDF file example).
To recap this, you can use any signed PDF document and create a document which contains arbitrary content in the name of the signing user, company, ministry or state.
Important: To verify the signature you need to trust the amazon.de certificate, which you would if you get signed PDFs from Amazon, otherwise the signature is still valid, but the certificate is not trusted. Furthermore, due to our responsible disclosure process, most applications already implemented countermeasure against our attack, you can find a vulnerable Adobe Acrobat DC Reader version here.
Who uses PDF Signatures?
Since 2014, organizations delivering public digital services in an EU member state are required to support digitally signed documents such as PDF files by law (eIDAS).
In Austria, every governmental authority digitally signs any document §19. Also, any new law is legally valid after its announcement within a digitally signed PDF. Several countries like Brazil, Canada, the Russian Federation, and Japan also use and accept digitally signed documents.
The US government protects PDF files with PDF signatures, and individuals can report tax withholdings by signing and submitting a PDF.
Outside Europe, Forbes calls the electronic signature and digital transactions company DocuSign as No. 4 in its Cloud 100 list. Many companies sign every document they deliver (e.g., Amazon, Decathlon, Sixt). Standardization documents, such as ISO and DIN, are also protecting by PDF signatures. Even in the academic world, PDF signatures are sometimes used to sign scientific papers (e.g., ESORICS proceedings).
According to Adobe Sign, the company processed 8 billion electronic and digital signatures in 2017 alone.
Currently, we are not aware of any exploits using our attacks.
How bad is it?
We evaluated our attacks against two types of applications. The commonly known desktop applications everyone uses on a daily bases and online validation services. The last one is often used in the business world to validate the signature of a PDF document returning a validation report as a result.
During our research, we identified 21 out of 22 desktop viewer applications and 5 out of 7 online validation services vulnerable against at least one of our attacks.
The corresponding CVEs are: CVE-2018-16042, CVE-2018-18688 and CVE-2018-18689.
You can find the detailed results of our evaluation on the following web pages:
How can I protect myself?
As part of our research, we started a responsible disclosure procedure on 9th October 2018, after we identified 21 out 22 desktop viewer applications and 5 out of 7 online validation services vulnerable against at least one of our attacks.
In cooperation with the CERT-Bund, we contacted all vendors, provided proof-of-concept exploits, and helped them to fix the issues.
You can take a look at which PDF Reader you are using and compare the versions. If you use one of our analyzed Desktop Viewer Applications you already should have got an update for you Reader.
My PDF Reader is not listed
If you use another Reader, you should contact the support team for your application.