Attacks on PDF Signatures
We developed three variants of the Shadow Attacks: Hide, Replace, and Hide- and-Replace.
Shadow Attack: Hide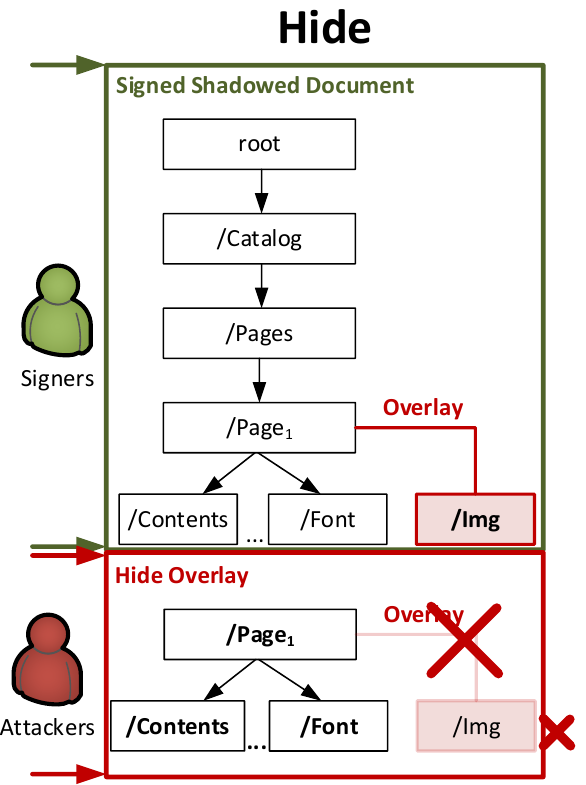
The concept of the Hide variant of shadow attacks is to hide the content relevant for the victims behind a visible layer. For example, the attackers can hide the text You are fired! behind a full-page picture showing Sign me to get the reward!. Once the attackers receive the signed document, they manipulate the document in such a way, that the picture is no longer rendered by the viewer application. Hide attacks have two advantages from the attackers’ perspective:
We identified two variants of this attack class: Hiding Content via Page. This attack variant uses an Incremental Update to create a new Page object. It contains all previously used objects except for the overlay, for example the image. This attack variant is depicted on the picture on the left side. Hiding Content via Xref. If the viewer application does not accept changes to PDF structuring objects, such as Page, Pages, or Contents, the second attack variant can be applied. This variant directly affects the overlay object by manipulating the Xref table. The simplest method for this is to create an Incremental Update, which only updates the Xref table by setting the overlay object to free. However, making this change is interpreted as a dangerous in many viewers (e.g., Adobe) and an error or a warning is thrown. For this reason, we use another approach: we use the same object ID within the Incremental Update, but we define it as a different object type. For example, we change the overlay type Image to XML/Metadata. Additionally, we added an Xref table update pointing to the metadata object, but keeping the object ID of the overlay. When opening this manipulated document, the overlay is hidden because Metadata cannot be shown. Since adding Metadata to assigned PDF using Incremental Update is considered harmless, the signature remains valid. All exploits can be downloaded here. |
Shadow Attack: Replace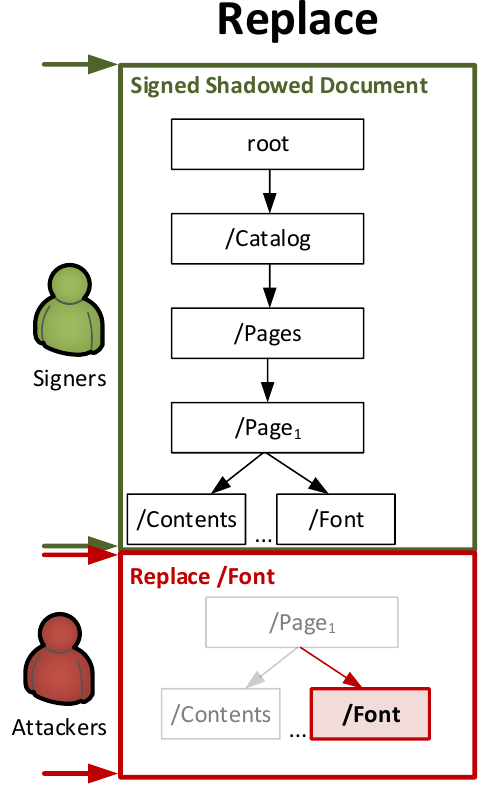
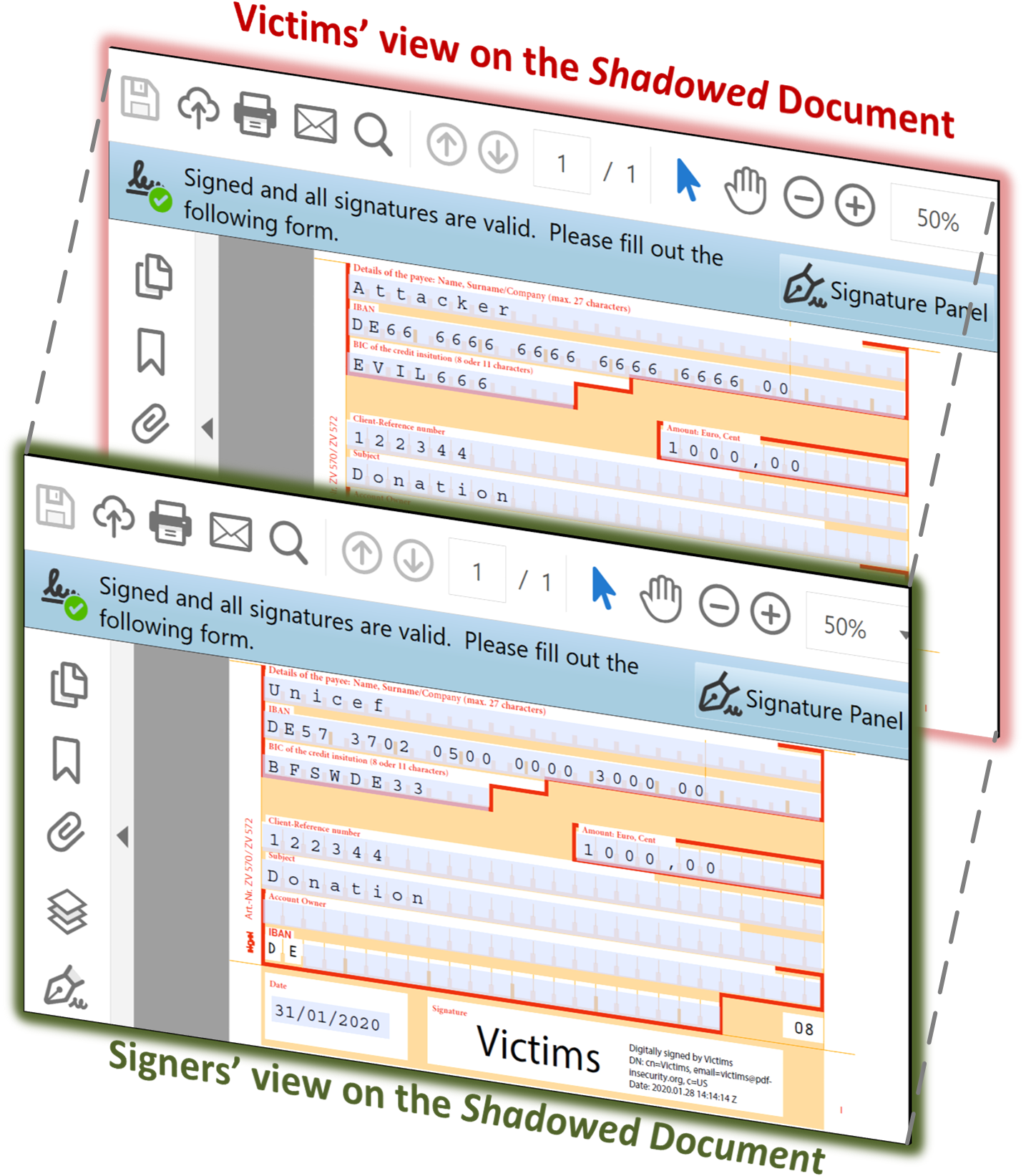
The main idea of the Replace variant is to append new objects to the signed document which are considered harmless but directly influence the presentation of the signed content. For instance, the (re)definition of fonts does not change the content directly. However, it influences the view of the displayed content and makes number or character swapping possible. Replace via Overlay. This attack targets an interactive feature in PDFs: interactive forms. Forms support different input masks (e.g., text fields, text areas, radio/selection buttons) where users dynamically enter new content and store it in the PDF document. Forms can also have default values which can be changed if needed. An example of a transfer slip as a PDF document containing forms is depicted on the figure on the right side. The main idea of the attack is to create a form, which shows one value before (PDF1) and after signing (PDF2). After the attackers manipulate the PDF and create PDF3, different values are shown in the form. The attack abuses a special property of PDF text fields. A text field can show two different values: the real field value and an overlay value which disappears as soon as the text field is selected. The real value of a form field is contained in an object key named /V. The content of the overlay element is defined within a /BBox object. The /BBox object is comparable to the hint labels known from HTML forms; for example the hint username to indicate that the username should be entered into a specific login field. In contrast to HTML, in PDF there is no visual difference between the hint and the actual value. Replace via Overwrite The attackers prepare a shadow document which defines a font and includes its description into the document, see the figure on the left side. The font is used for the presentation of a specific content. After the document is signed, the attackers append a new font description and overwrite the previous description. Since, the definition of new fonts is considered harmless, the applications verifying the signature does not show any warning regarding the made changes. All exploits can be downloaded here. |
Shadow Attack: Hide-and-Replace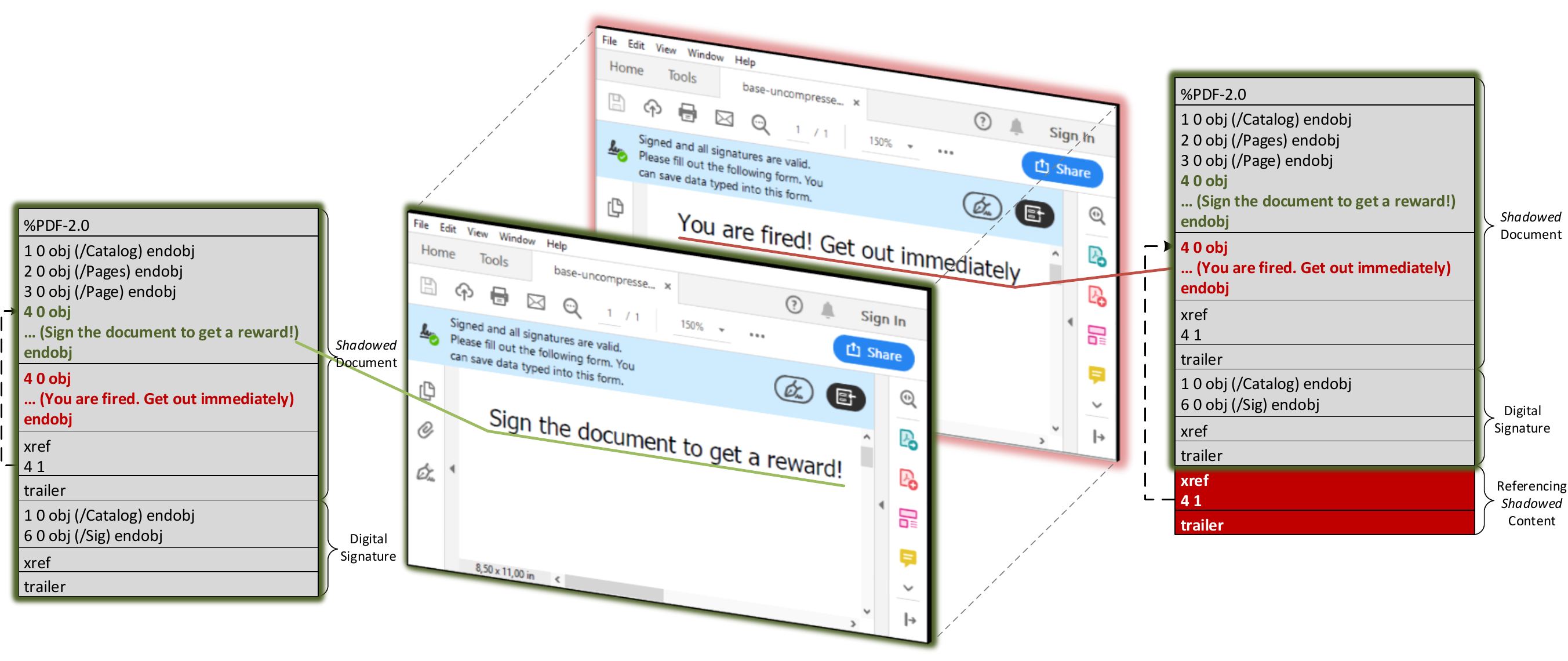
In Hide-and-Replace attack variant, the PDF document contains a second, hidden document with different content. Since the signers cannot detect the hidden (malicious) content, they sign the document. After signing, the attackers receive the document and append only a new Xref table table and Trailer. Within the Xref table table, only one change takes place: the reference to the Description. An example of the attack is depicted above and will be further explained.
Advantages and Disadvantages. The Hide-and-Replace attack variant is the most powerful one since the content of the entire document can be exchanged. The attacker can build a complete shadow document influencing the presentation of each page, or even the total number of pages, as well as each object contained therein. A possible disadvantage could occur if during the signing process,unused objects are removed. Thus, the shadow elements could be deleted, making the second step of the attack obsolete. A security scanner could also detect the unused objects within the PDF and throw a warning. Currently none of these disadvantages occur. All exploits can be downloaded here. |