Universal Signature Forgery (USF)
The main idea of USF is to disable the verification by providing invalid content within the signature object or removing the references to the signature object. Thus, despite the fact that the signature object is provided, the validation logic is not able to apply the correct cryptographic operations. Nevertheless, it could be possible that a viewer shows some signature information although the verification is being skipped.
Technically, each PDF Signatures is defined in a PDF signature object, e.g., 5 0 obj. Without going into too much details, this object contains all information necessary to validate the signature. Most importantly for out attacks, the signature object contains a /ByteRange entry, which defines the offsets of the bytes used to compute the hash of the signature. The signature itself is then stored in a /Contents entry as a PKCS7 blob (in most cases).
The USF attack manipulates those entries in the signature obj to confuse the signature validation logic, as shown in the picture below.
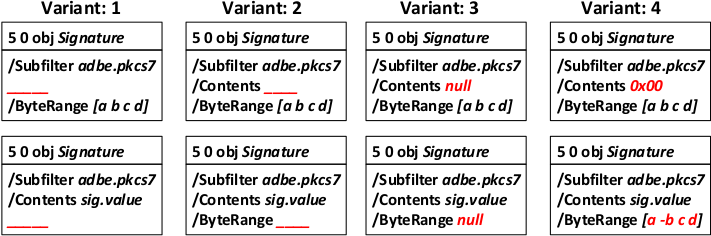
If the attack is successful, the view application (or the online validation logic) will display a panel that the signature in the contained PDF is valid and belongs to a specific person or entity.