CBC Malleability
While partial encryption works on unmodified ciphertext and adds additional unencrypted strings or streams, CBC gadgets are based on the malleability property of the CBC mode. Any document format using CBC for encryption is potentially vulnerable to CBC gadgets if a known plaintext is a given, and no integrity protection is applied to the ciphertext.
A CBC gadget is the tuple (Ci −1, Ci ) where Ci is a ciphertext block with known plaintext Pi and Ci −1 is the previous ciphertext block. We get Pi = dk (Ci ) ⊕ Ci −1 where dk is the decryption function under the decryption key k . An attacker can gain a chosen plaintext with Pc = dk (Ci )⊕ Ci −1 ⊕ Pi ⊕ Pc. An attacker can inject multiple CBC gadgets at any place within the ciphertext and can even construct entirely new ciphertexts.
Missing Integrity Protection
The PDF encryption specification defines several weak cryptographic methods. For one, each defined encryption algorithm which is based on AES uses the CBC encryp- tion mode without any integrity protection, such as a Message Authentication Code (MAC). This makes any ciphertext modification by the attacker undetectable for the victim.1 More precisely, an attacker can stealthily modify encrypted strings or streams in a PDF file without knowing the corresponding password or decryption key. In most cases, this will not result in meaningful output, but if the attacker, in addition, knows parts of the plaintext, they can easily modify the ciphertext in a way that after the decryption a meaningful plaintext output appears.
Building CBC Gadgets
A necessary condition to use CBC gadgets is the existence of known plaintext. Fortunately – from an attacker’s point of view – the PDF AESV3 (AES256) specification defines 12 bytes of known plaintext by encrypting the extended permissions value using the same AES key as all streams and strings.
Although the Perms value is encrypted using the ECB mode, the resulting ciphertext is the same as encrypting the same plaintext using CBC with an initialization vector of zero and can, therefore, be used as a base CBC gadget.
Furthermore, the AESV3 encryption algorithm uses a single AES key to encrypt all streams and strings document-wide, allowing the use of gadgets from one stream (or the Perms field) in any other stream or string. For older AES-based encryption algorithms, the known plaintext needs to be taken from the same stream or string which the attacker wants to manipulate.
Content Injection
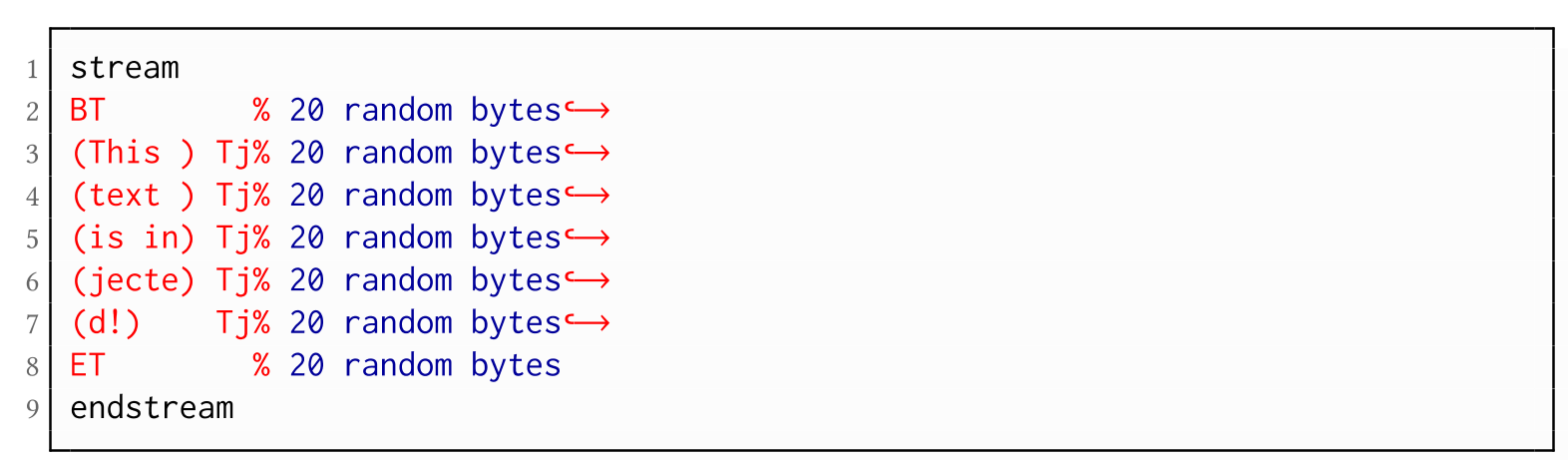
Using CBC gadgets, an attacker can inject text fragments into an encrypted PDF document. This injection is possible by either replacing an existing stream or by adding an entirely new stream. The attacker is able to construct and add multiple chosen plaintext blocks using gadgets. However, every gadget constructed from the 12 bytes of known plaintext from the Perms entry leads to 20 random bytes: 4 bytes of random from the Perms value itself and 16 bytes due to the unpredictable outcome of the decryption of the next block of ciphertext. Fortunately, most of the time, these random bytes can be commented out using the percentage sign character (i.e., a comment).